In an increasingly digitized world, user authentication is crucial, especially in the world of financial services. The regulations of the Second Payment Services Directive (PSD2) impose certain compliance rules in this area, as Strong Customer Authentication (SCA) is a guarantee of security.
Its implementation represents a strategic challenge and requires technical and regulatory expertise. Discover SCA’s best practices for securing your financial operations.
What is strong authentication?
This is a regulatory obligation that applies to all financial institutions on European territory from 2019.
In order to enhance the security of online payments and electronic financial transactions, SCA was initially introduced by the PSD2 Directive under EU Directive 2015/2366. Subsequently, the European Commission issued a complementary regulation, Delegated Regulation (EU) 2018/389, to specify the technical aspects of implementing strong authentication. This method for authenticating users is based on the principle of implementing several actions to ensure that the end user is indeed the “owner” of the account involved and the “initiator” of the requested operation. The initial 90-day deadline for renewing strong customer authentication has been extended to 180 days since July 25, 2023, via EU delegated regulation 2022/2360.
A regulatory update
The principle of strong authentication aims to foster innovation in the payment industry while protecting consumers and their transactions.
It involves using a combination of at least 2 out of three types of factor to validate any remote operation. These factors must be implemented in such a way that if one is compromised, it does not affect the other.
In practical terms, all regulated payment and e-money institutions are required to set up appropriate systems for their customers (individuals and businesses).
It should be emphasized that agents working under Treezor’s license are responsible for ensuring that authentication measures are properly implemented, and Treezor is responsible for ensuring that they comply with current regulations. In the event of situations requiring improvement identified during audits or controls, this would have an impact on both agents and Treezor. It is with this in mind that Treezor pays particular attention to this subject, in the interests of cooperation and mutual reinforcement.
On June 28, 2023, the European Commission reaffirmed the importance of strong authentication when it published its proposals for PSD3 and the future Payment Services Regulation (PSR). It plans to include SCA in the PSR so that it automatically applies to all member states.
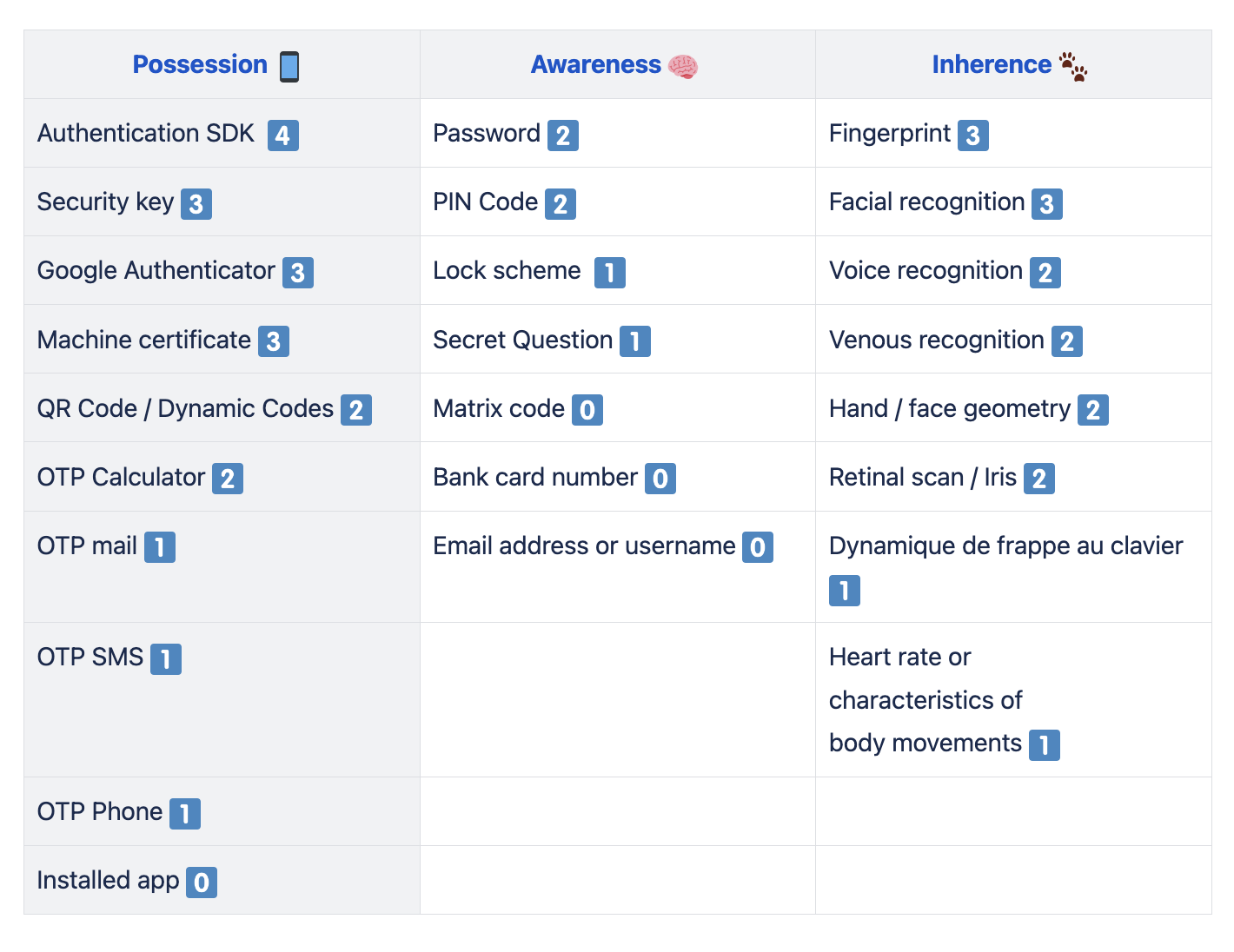
Authentication factors
According to the Regulatory Technical Standards (RTS), strong authentication is based on the validation of at least two factors from three categories.
➔ Knowledge: this is something that only the user knows, such as a password, PIN code or the answer to a secret question.
➔ Possession most often means an object the user owns, such as a smartphone or a secure key.
➔ Inherence refers to a characteristic that is inherently inseparable from the user, such as a fingerprint, facial or voice recognition…
In practice, to validate an online purchase, for example, consumers log on to their bank’s mobile application from their smartphone (what I own), then enter a secret code (what I know) or their fingerprint (what I’m known for). Without the successful completion of these two steps, the transaction is rejected.
How can I be sure of choosing the right authentication factors?
Current regulations require the use of two authentication factors during transactions, but the choice of these factors can be complex due to the variety of options available, each with its own advantages and disadvantages. Selecting the right authentication factors can therefore be tricky.
To simplify this process, Treezor set up a specific tool to check or validate the robustness of the factors. Each factor has been assigned an evaluation based on a balance between reliability and user-friendliness. These ratings reflect Treezor’s assessment of a factor’s implementation in line with the safety standards required by the regulator. To check the compatibility of your combination with Treezor’s approach, please follow the steps below:
- Select two factors from two different columns
- Add up the scores for each factor (note that a factor of 0 cannot count as a valid authentication factor).
- If your combination obtains a result > 5: congratulations, your solution is reliable and user-friendly.
- If your combination is between 4 and 5: bravo, you’re SCA-compliant, but your factors are a little unreliable or make the user experience more cumbersome.
- Your combination is equal to 3: you’re still compliant, but your factors are starting to increase your risk profile and your user paths are degraded.
- Your combination is equal to 2: your risk profile is too high, so you’ll have to select other factors.
Table updated in August 2023
Operations covered by SCA
The use of strong authentication depends on the transaction’s level of exposure to the risk of fraud. There are several scenarios.
➔ SCA on first account login and every 180 days: the user authenticates themself using two factors every 180 days. When it comes to the interval between two renewals, the strong authentication exemption applies: customers can access information concerning the last three months of transactions on their bank accounts, and view the balance with their usual password. The aim of this measure is to strike a balance between security and user-friendliness, and to provide end-users with a more pleasant, less time-consuming customer experience.
➔ SCA with active session: these are sensitive operations that can be carried out one after the other while the session is active: displaying RIB (bank account details), ordering a card, etc.
➔ SCA for every so-called critical remote transaction that could cause financial loss: adding a beneficiary, executing a SEPA credit transfer, making a credit card payment, etc.
However, not all payments require strong authentication, and in some cases other transactions considered low risk can benefit from a smoother payment experience.
Why adopt SCA? Secure your financial operations
In phishing scams, the fraudster assumes the visual identity of an official organization (tax office, bank, etc.) and asks for payment card details to be updated. SCA aims to protect consumers who fall prey to this type of computer attack and the hacking of their bank details.
According to the European Central Bank’s 2023 report, card payment fraud has fallen sharply. In 2021, the proportion of card payment fraud to the total value of card payments in the SEPA zone reached its lowest level (0.028%) since 2008 (when the Eurosystem began collecting such information from card acceptance networks (schemes).
This sharp drop reflects the beneficial impact for clients of regulatory technical standards regarding strong customer authentication under the revised EU Payment Services Directive (PSD2).
In this way, SCA helps to build a climate of trust between companies and consumers, and enhances the security of sensitive operations.
However, new fraud techniques, based on manipulation, are emerging to circumvent SCA. For example, spoofing is on the rise: the fraudster impersonates a bank advisor during a telephone call to obtain strong authentication for a transfer or card payment.
It is therefore essential to support end-users in the vigilance process, so that they comply with certain best practices in terms of data retention and communication.
How to set up SCA? Best practices
Implementing SCA requires a judicious choice of authentication factors. It involves finding the right balance between reliability and ease of use in the customer journey, to avoid transaction rejection and friction points with the user.
Treezor’s SDK (Software Development Kit) solution for the cryptographic safe combines security and a seamless customer experience, to optimize the implementation of strong authentication. Once integrated into the mobile application, the SDK is capable of signing and encrypting to guarantee the authenticity and integrity of the initial request (sensitive operation) issued by the end user. In general, Treezor’s SCA solution provides irrefutable proof of strong authentication, guaranteeing both the possession factor and the inherence (biometrics) or knowledge factor.
For user experience and security improvement reasons, we recommend the biometric factor rather than the knowledge factor. Once the smartphone has been registered, a PIN code or facial recognition can be associated. In the absence of a cell phone, financial institutions can offer a security key.
Biometrics corresponds to the inherence factor. Among the many potential examples, fingerprint and facial recognition are complex to reproduce and therefore effective in a strong authentication procedure.
Knowledge can take the form of a password, PIN code or secret question. However, this type of information is easily hacked. We recommend a strong password, with random alphanumeric characters and sufficient length.
Switch to strong authentication with Treezor!
Complying with the principle of strong authentication is first and foremost a means of complying with current regulations (DSP2 and RSP) and protecting the end user, whether a company or an individual. SCA reduces the risk of fraud and contributes to the development of the digital economy.
Treezor supports you in the implementation of SCA according to your specific needs, offering a personalized approach from the project study stage through to the entire implementation process. To ensure a smooth transition to SCA, migration is carried out in stages.
If you’re still unsure about which factors to adopt, Treezor is here to help you select the optimum combination of reliability and quality user experience. What’s more, you’ll be informed of the various ways to raise awareness among your users to protect them against identity theft.
Would you like to implement strong authentication and secure your login and payment operations? Our experts are available to discuss your project.